Consistently, similar to precision, Apple delivers another telephone and another iOS for all current iPhones. This year, we invited iOS 12. This is a period of incredible energy for iPhone clients; new working frameworks mean new highlights, Norton error 3048, applications, and then some. With all these new improvements, it’s imperative to remember that these new highlights may help or obstruct your security and protection. We investigated the new iOS and accumulated a few hints and deceives to help secure your gadget, your information, and your secret phrase use.
1. Turn on USB Restricted Mode
USB Restricted Mode is a more up to date highlight on iOS that you may not think about yet. This security highlight forestalls USB embellishments that plug into the gadget from making information associations with an iPhone, iPad, or iPod. This forestalls designated “juice jacking,” which is when malware can be introduced onto a gadget or data can be taken employing the USB charging port.
Step by step instructions to turn on USB Restricted Mode:
Settings > Touch ID and Passcode > type in your password. Look down and guarantee that the “USB Accessories are not allowed on the lock screen” setting is off
2. Ensure programmed iOS refreshes are turned on
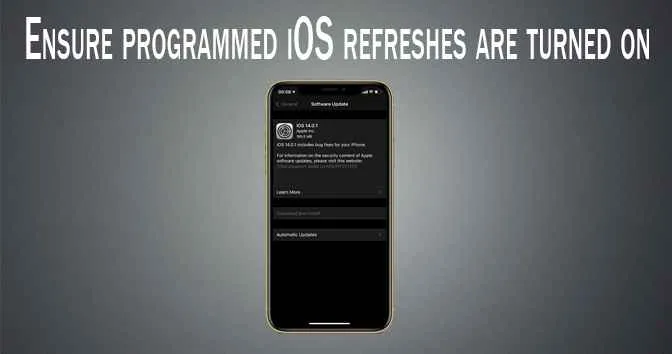
Refreshing applications and working frameworks are critical to the security of your gadget. They add norton sonar protection updates, and they additionally address what is known as a product weakness. A product weakness is a security opening, or shortcoming, in a working framework or programming program. Programmers can abuse these shortcomings by composing code to focus on a particular weakness. These endeavors could taint your PC with no activity on your part other than survey a Norton error 3048 3, opening an undermined message or playing contaminated media.
The most effective method to check if programmed refreshes are turned on:
Settings > General > Software Update and turn on programmed refreshes.
3. Empower Find My iPhone



Discover my iPhone is Apple’s inherent following programming. It utilizes GPS to find a lost or taken telephone. Notwithstanding helping discover a telephone, it likewise has other inherent security highlights, for example, Activation Lock, which will forestall any other individual from utilizing your iPhone.
To get entrance, it requires the client’s Apple ID and secret word. Without this data, somebody can’t kill the Find My iPhone include deleting your gadget or reactivate and utilizing your Norton error 3048 3.
Also Read – How to fix Norton error 8504 103
4. Incapacitate lock screen choices


The iPhone’s lock screen has designated “gadgets” that permit speedy admittance to certain highlights, such as your camera, wallet, and Wi-Fi and Bluetooth associations. While they don’t permit a client full admittance to the telephone, somebody can look at present swipe some close to home data with those highlights.
Step by step instructions to incapacitate lock screen:
Settings > Control Center, and switch off which gadgets you don’t need to be got to in the lock screen.
5. Utilize a VPN on open Wi-Fi



A virtual private organization gives you a private and secure approach to interface with the web any place you use it. It makes a protected, encoded association between your public web association and the VPN administration’s private worker.
A Norton error 3048 3 goes about as such a passage, encoding the information you communicate and getting while on open Wi-Fi, such as at a coffeehouse or air terminal.
6. Go through extra encryption when backing
Your touchy information is on your telephone. In addition to the fact that you want to keep a duplicate of it, you’ll need to help ensure that information. When sponsorship up your Apple gadgets, it’s ideal for interfacing with your PC and using iTunes. Ensure iTunes is set up to scramble those reinforcements. Thusly, this scrambles your information, and you can make a different secret word.
7. Screen protection settings intermittently
Some of the time, we introduce applications that are utilized for a brief timeframe and afterward end up staying there occupying a room on your telephone. You might need to play out a review of those applications since they could likewise represent a security hazard on your telephone.
Undesirable applications could deplete your battery and hinder your gadget. At times the protection arrangements in applications change. This could represent a security concern except if you read the fine print cautiously.
The most effective method to screen security settings:
Settings > Privacy. Here dwells the expert rundown, everything being equal, alongside which applications you’ve allowed them to. Experience every one of them occasionally and deny any consents you don’t think a specific application needs.
8. Set a more grounded gadget password
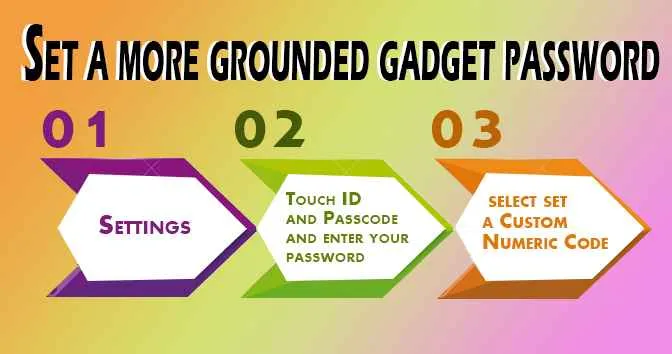


As a matter of course, the iPhone has a four-character numeric password. Did you realize that now you can change that and utilize alphanumeric passwords on your telephone?
The most effective method to set a more grounded gadget password:
Settings > Touch ID and Passcode and enter your password > select set a Custom Numeric Code.
9. Set up two-factor verification


Two-factor verification, otherwise called 2FA, is a technique for confirming your character that adds a second type of validation notwithstanding your record secret key. It comprises of two of the accompanying three things: Something you have: an ATM or Mastercard, cell phone, or security token, for example, a key dandy or USB token.
The most effective method to set up 2FA:
Settings > tap your name > Password and Security. Tap “Turn on Two-Factor Authentication” and follow the prompts.
10. Use Touch ID or Face ID


Notwithstanding a solid password, you can add another security layer by empowering both Touch ID and Face ID, if accessible. The most effective method to set up Touch ID or Face ID:
- Settings > Face ID and Passcode. Whenever asked, enter your password.
- Tap “Set Up Face ID,” at that point, adhere to the on-screen directions.
- Settings > Touch ID and Passcode, at that point, enter your password.
11. Ensure your iPhone screen bolts rapidly



The most secure alternative is to set Require Passcode to Immediately, which will require you or any individual who gets your telephone to enter your password regardless of how quite a while in the past you last opened your telephone.
Also Read – Top 5 Antivirus and Security Apps For iPhone 5 and iOS Devices
Step by step instructions to set up Auto-Lock:
Settings > General App > Auto-Lock
12. Change your reused passwords
iOS 12’s secret key director has another component: secret key evaluating. One of the primary troubles with passwords is choosing special passwords for every record we use.
Lamentably, that standard isn’t constantly followed, and Apple’s new secret word reviewing highlight helps make dealing with all your extraordinary passwords a lot simpler. This component will review your put away passwords and let you know whether you have any copies.






