Hackers take over your social media accounts, using them from basic spam to drawing attention to international issues. Even ifRead More
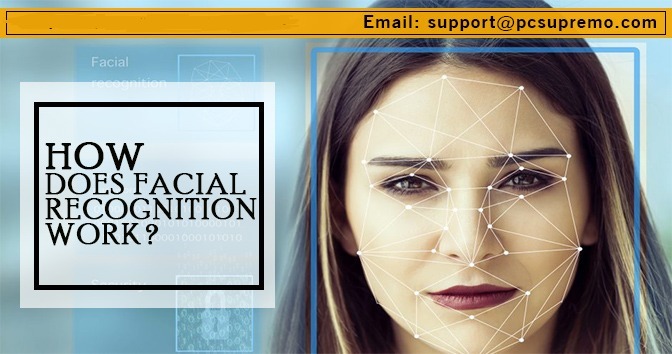
How does facial recognition work?
Facial recognition refers to the features of several Android and Windows system that allows them to open only when aRead More
What you need to do about the WPA2 Wi-Fi network vulnerability
WPA 2 stands for Wi-Fi Protected Access 2. At the same time, Wi-Fi stands for wireless fidelity. It is theRead More
Biometrics and biometric data. What is it, and is it secure?
Biometrics are the features of several security software and applications that enable them to store facial, fingerprint, and physical andRead More
What is Ransomware and How to Prevent Ransom-ware attacks?
Ransom-ware has been the cause of major wide-scale attacks in the global IT arena. Norton sonar protection has been a major helpRead More
Why your online privacy matters?
Security is defined as the safety measures taken to remain protected to provide extra and adequate certainty. In general, weRead More